Little Known Questions About Edge Networking.
Table of ContentsThe 7-Second Trick For Edge NetworkingThe Best Guide To Edge NetworkingThe Best Guide To Edge NetworkingEdge Networking Things To Know Before You Get ThisThe Only Guide to Edge NetworkingGetting My Edge Networking To Work
It's simple to see that edge compute will be decreasing expenses over traditional cloud infrastructure the more that calculate can be removed of origin servers, the lower the expenses needed on infrastructure and bandwidth to deal with peak need. Considering that edge calculate puts computing & storage abilities exceptionally near to endpoints, there are extremely specific cases this aids with.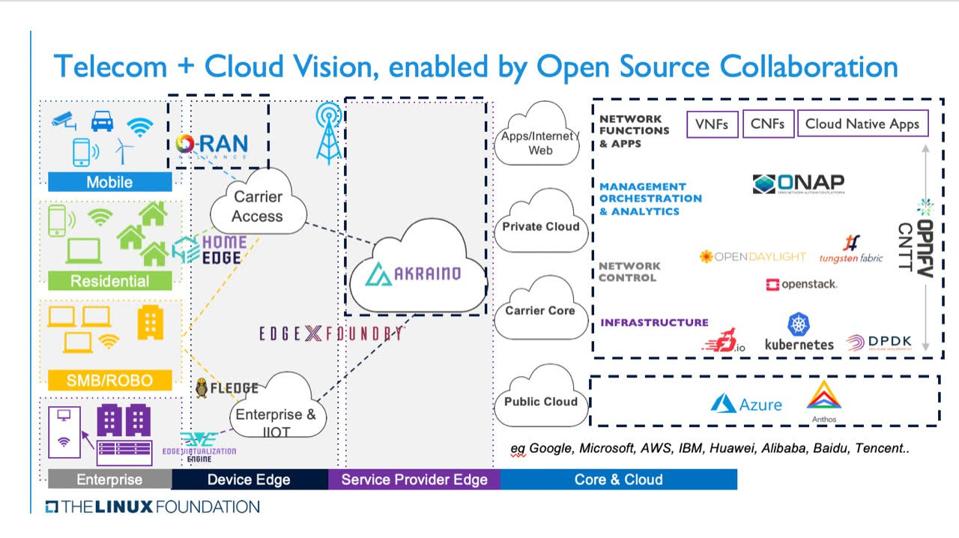
Now they can run custom-made code out in the edge, too, in order to make sensible decisions anywhere throughout that network. They can be making compute-intensive decisions, not from one end or the other, based on the request or its metadata (context). Certain users or device types, or certain geo-locations, can take various courses in the networking and in the content routing.
Not known Facts About Edge Networking
Companies might do A/B user testing, by sending a subset of users to different systems in order to check new features. This is all already possible to a little degree in existing CDNs with programmable networks, however edge computing considerably enhances the quantity of computational reasoning that can be used, anywhere throughout the edge network.
Edge networks currently protect all the traffic in between the edge entry points (edge-to-edge). Traffic can take a trip securely many of the way around the world totally within their edge network, so that the only part of the journey that is unprotected is beyond the edges of their network the Last Mile on either end.
In order to supply protection end-to-end, they have actually produced applications to safeguard the endpoint to the closest edge server (Last Mile of gadget), and from the nearby edge server to the business service being protected (Last Mile of business bandwidth). By producing safe tunnels extending their edge network on both ends,.
Our Edge Networking Ideas
Both Zscaler and Cloudflare provide services that protect all traffic end-to-end across the entirety of their global edge network. Traffic from endpoints securely enter their global network and are now able to be protected all the method to the last destination (SaaS service, internal APIs, etc), then back once again. They are securing both outgoing requests (from a client's users to the SaaS services they utilize), and incoming requests (from a consumer's customers or labor force to the internal services they make use of).
Their item goes an action even more, and brings Cloudflare's platform directly onto your business network. They then included another item,, to safeguard incoming traffic, permitting users to securely access a company's origin server, regardless of where it lives (in the cloud or an on-prem data center). This is achieved through No Trust capabilities they have actually built, which are possible due to the software-defined networking architecture they've embraced.
So Cloudflare then created a additional info Secure Web Entrance (SWG) item called, to secure the traffic from the endpoint making requests to the SaaS services that an enterprise utilizes. Between outbound traffic production in Gateway and incoming traffic security in Access, Cloudflare now offers end-to-end security of network traffic for a business's users.
The 7-Minute Rule for Edge Networking
They protect outbound traffic from endpoints to external servers (ZIA, their Secure Web Entrance) and inbound traffic from endpoints to origin servers (ZPA, their Absolutely no Trust protected gain access to approach). Cloudflare developed their Gateway and Access products into a brand-new competiting platform called. [See more information on Cloudflare for Teams in my Cloudflare deep dive from March.] This reveals what type of architecture utilize these edge networks (aka edge cloud platforms) truly have.
Note that in reaction to the pandemic, Cloudflare happened to make this brand-new product line complimentary for the first 6 months. Edge Networking. Last earnings, they kept in mind that they already have 1000 clients on it, so I anticipate the business to see start seeing a revenue increase in Q420. In navigate to these guys addition, their end-to-end security platform appears to be a lot easier to release than Zscaler's, which is intricate enough to greatly require system combination partners.
However simply today, they published a tech blog site entry highlighting their extreme concentrate on security-- so it is plainly at the leading edge of their minds. I would anticipate them to eventually move into this market, simply as Cloudflare has currently done, and the post provided us a major tip that "there's more to come on that quickly".
The Best Guide To Edge Networking
Their users and their utilized services can intermingle as needed, managed by an IAM service like Okta. I expect Cloudflare for Teams to begin getting promoted in this exact same direction, as it is a product line that is not only perfect to protect a business's internal workforce, but also to protect the partnerships they have with others.
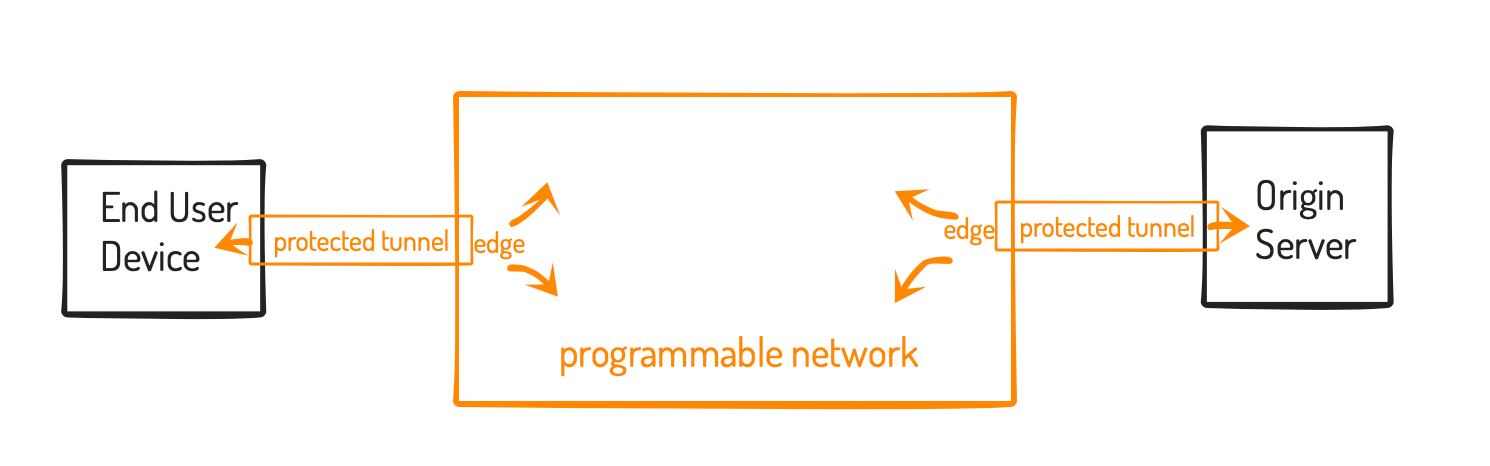
Return to my Singapore latency above. An endpoint in Singapore running a complex app with consistent intercommunication could be talking to an edge server that is 12ms away, rather of 275ms away. That difference is massive when dealing with two-way bandwidth- and compute-intensive use great post to read cases, like sophisticated video gaming and AR/VR.
The Best Strategy To Use For Edge Networking
Edge calculate could be making decisions around how to finest preserve latency, such as stepping down the bandwidth requirements of a feed until the maximum combination is found, or reducing all of your traffic speeds across all at the same time taking place network requests when you are nearing bandwidth capability. Given that the latency is so low, the edge servers can much better tie to being an extension of the endpoint device itself.